Online communication predominantly uses the DNS to look up information. DNSSEC secures the DNS protocol, thereby improving the security of overall online communication. We explain this is more detail below.
How does the DNS (Domain Name System) work?
The DNS can be pictured as a globally distributed telephone directory, which allocates the globally unique domain names (switch.ch) to the globally unique internet addresses (IP addresses like 130.59.138.34). The domain names are used simply because they are easier to write.
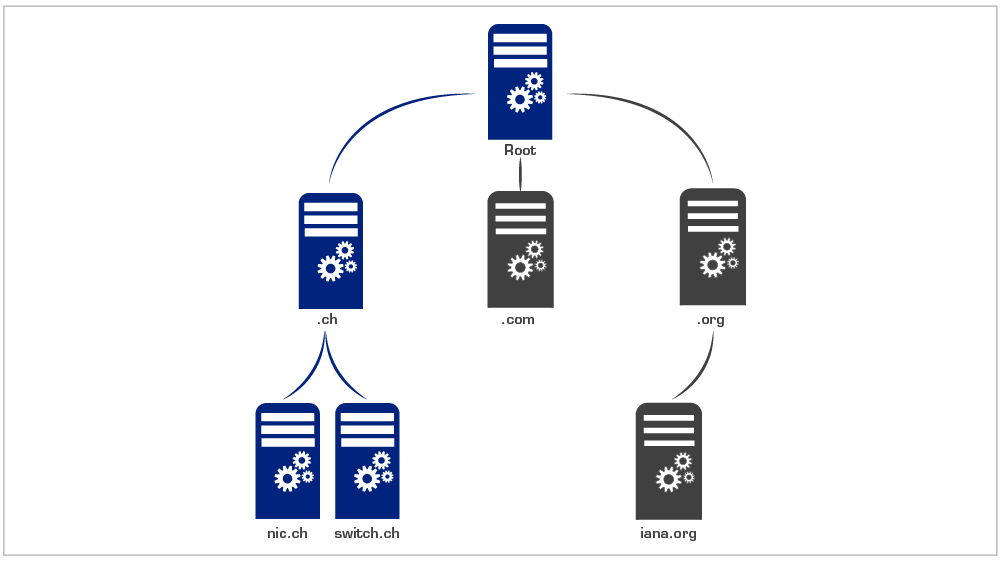
To make sure that the different queries do not all land up on the same server, the DNS is designed with a hierarchical structure. The name space is divided up into so called zones. In the case of www.switch.ch, the top level of the hierarchy ("root zone") would be followed by the servers for Switzerland ("ch"), and then the Switch servers ("switch.ch"). The competences of the individual zones are divided up (delegated) within the hierarchy.
When you want to access the website www.switch.ch on your computer, your internet provider's name server queries all levels of the hierarchy described above one after the other. Each level that cannot answer the query about the destination address provides information to the next level down. The server at the bottom of the hierarchy can then supply the IP address of the destination server.
What is the purpose of DNSSEC?
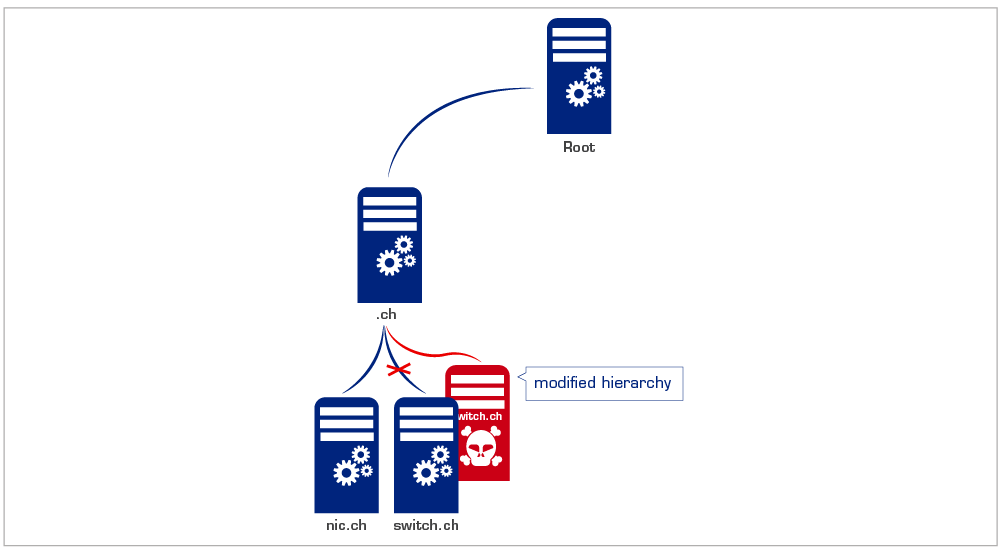
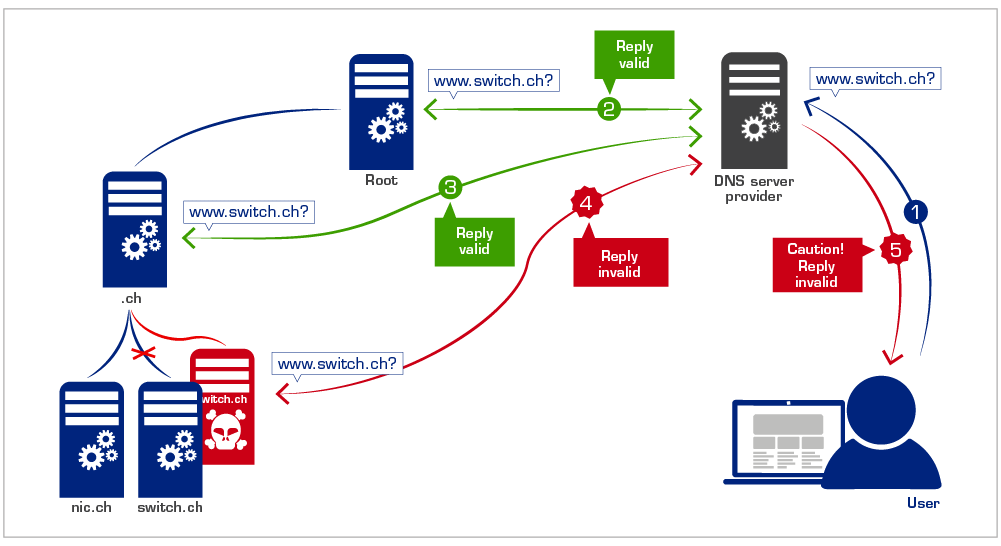
Imagine a situation where someone succeeds in changing entries in the telephone directory. You thus look up the number for Switch and find the wrong number listed there. Would you have had any means of recognising this non permitted abuse? Not really. Such a scenario would be possible in the internet if an attacker were to change the hierarchy described above. If an attacker succeeds, for instance, in smuggling incorrect data into your provider's server (Cache Poisoning), then you would land at a different website when you called up www.switch.ch. It's best not to try and imagine what could happen if the forged website was your bank's. Or if you were to send your company's latest strategy to a Partner's "forged" mail server.
Since the internet is used for a whole range of different purposes today, hacker attacks can have far-reaching implications. DNSSEC provides fundamental protection against attacks of this type – and not only when websites are called up.
DNSSEC cannot protect against phishing attacks on a general basis. It does, however, provide efficient protection against attacks on the DNS. This is what is important, since most phishing attacks can be recognised and prevented by alert internet users. Even experts, however, can scarcely detect attacks on the DNS.
How does DNSSEC work?
DNSSEC is based on cryptographic signatures with which the current DNS entries are signed. Anyone who is responsible (authoritative) for a domain name in the internet can protect their information by means of DNSSEC. All the information for which a service provider holds responsibility is signed with this service provider's private key, and the signatures are written in the DNS (RRSIG Record).
An example with DNSSEC
Your internet provider's name server once again follows the familiar hierarchy in order to resolve a query. This time, however, it can check on the basis of the signatures received whether the origin of the answers is correct and whether an answer has been modified en route. The name server will only answer if all the information is correct.
How is it possible for all these signatures to be checked?
To compile digital signatures, a pair of keys is generated. A pair of keys of this type is made up of a private and a public key (asymmetric cryptosystem). As the name suggests, the private part is secret and remains with the owner. The public part is published in the DNS (DNSKEY Record). Using the public key, it is now possible to check and validate a signature that has been signed with the private key.
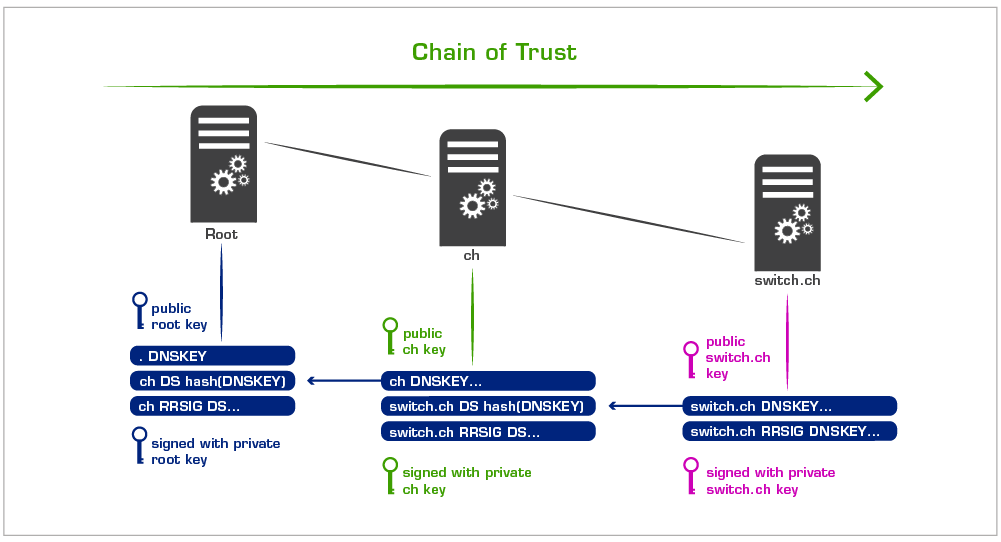
It is thus necessary to trust a public key before you can check a signature. Since it is not possible to trust all the keys in the internet, use is made of a key hierarchy similar to the DNS hierarchy, the "Chain of Trust". This looks somewhat confusing at first sight, but its sole purpose is to ensure that all signatures can be verified with a single public key.
The "Chain of Trust" in detail
An image of the public key is notified to the next level of the hierarchy. The higher level writes this image into its zone (DS Record) and guarantees its authenticity by signing it. The public key for this level is then, in turn, notified to the next higher level.